“D33DS Company” Hackers Release Info from 453,492 Yahoo! Accounts
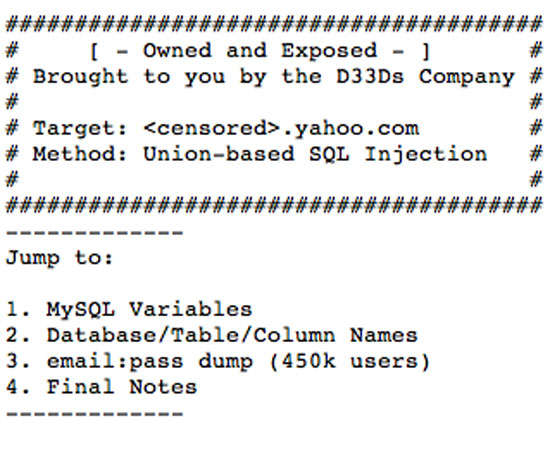
Ars Technica is reporting that usernames and passwords allegedly from Yahoo! were posted online by the D33DS Company group. Other sources indicate that the user information was specifically from the Yahoo! Voice service, formally known as Associated Content.
Apparently, the hackers were able to obtain the plaintext list of passwords and usernames using a MySQL injection attack. Ars explains the methodology behind the attack thusly:
The hacking technique preys on poorly secured web applications that don’t properly scrutinize text entered into search boxes and other user input fields. By injecting powerful database commands into them, attackers can trick back-end servers into dumping huge amounts of sensitive information.
At the end of the dump is a note from D33DS Company, which reads:
We hope that the parties responsible for managing the security of this subdomain will take this as a wake-up call, and not as a threat. There have been many security holes exploited in webservers belonging to Yahoo! Inc. that have caused far greater damage than our disclosure. Please do not take them lightly. The subdomain and vulnerable parameters have not been posted to avoid further damage.
Unfortunately, the D33DS Company website is having some trouble staying online as of writing. However, it does appear to contain the reported list of credentials. Also, if you think that “thx1138” is a unique password, you’re wrong.
However, a fully searchable version of the list — sans passwords — is up on Dazzlepod. If you’re concerned that your account may have been compromised, you can search for username and see if it pops up on the list.
(Ars Technica via Techmeme)
- BMW keyless entry system hacked in three minutes
- Turns out drones are super easy to hack
- Scientists crack SecurID tokens
Have a tip we should know? tips@themarysue.com